Malvertising can take on several forms. At its most dangerous, the malware itself can be injected in advertisements, such that the second the user loads the script, they are infected. In this case, malware brokers are using Google Ads (which do not permit custom scripts) to advertise websites which offer malicious binaries for the user to download.
“Threat researchers are used to seeing a moderate flow of malvertising via Google Ads,” volunteers at Spamhaus wrote on Thursday. “However, over the past few days, researchers have witnessed a massive spike affecting numerous famous brands, with multiple malware being utilized. This is not ‘the norm.’”
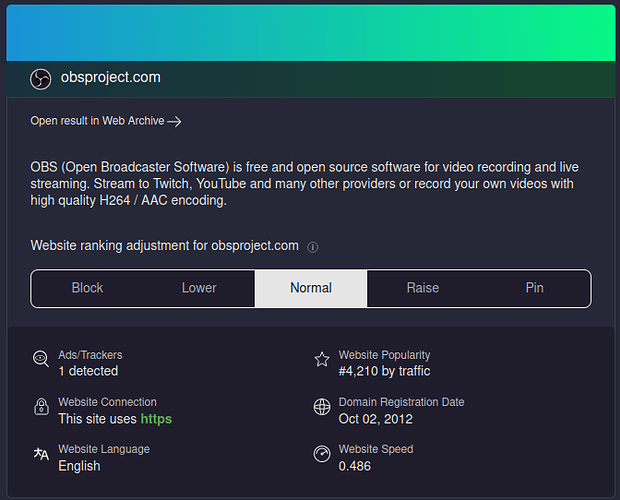
Over the past month, Google Ads has become the go-to place for criminals to spread their malicious wares that are disguised as legitimate downloads by impersonating brands such as Adobe Reader, Gimp, Microsoft Teams, OBS, Slack, Tor, and Thunderbird.
I’ve been hearing this story for a few weeks, and I was initially surprised it was deemed newsworthy. However, I then considered that, for a lot of people, search engines are where they get all of their information from. And Google is the most widely-used search engine. This isn’t just a case of widespread naivete; technical users can make this mistake.
(Click to Expand) The first form of malvertising implemented with malicious scripts can be avoided by blocking Javascript by default and enabling it for trusted sites.
You can use uBlock Origin to do this, but Noscript might be preferable for some users. Using an ad-blocker with pre-loaded lists without disabling Javascript wholesale will *not* prevent malvertising. It will prevent *known* malvertising. Enumerating badness, which is the method ad-blockers primarily use, will not successfully block *all* unwanted scripts.See #2 - Enumerating Badness for an in-depth explanation of why this is a dumb idea, but also why ad-blockers need to use it: The Six Dumbest Ideas in Computer Security
Ad-blockers are a convenience, not a security tool.
The form of malvertising appearing in Google cannot be avoided this way. You need some way of determining the domain is legitimate, and if your primary method of checking whether something is legitimate is using a search engine…that’s not going to help here.
If you want to quickly verify a domain name is legitimate, one way is to visit the Wikipedia page. For example, if you wanted to know that gimp.org is the official homepage for the GIMP software, you could visit the wikipedia page to confirm this: GIMP - Wikipedia
This isn’t a silver bullet, but it’s better than doing nothing. Perhaps check for recent edits in the history of the page to ensure the webpage hasn’t been changed recently. Of course, this won’t work for lesser-known sites.
If you’re using Kagi, the summary it gives you when you click on the shield can be helpful: